Real Tips About How To Detect Buffer Overrun

This topic describes how a c/c++ query for detecting a potential buffer.
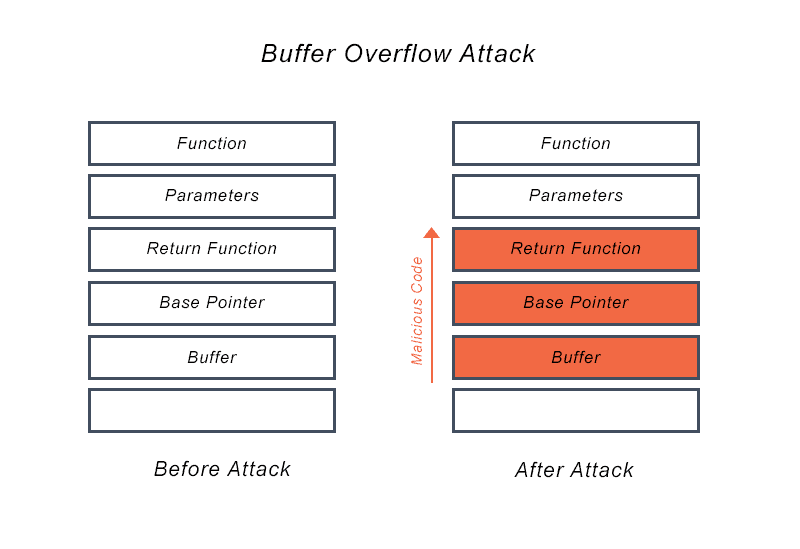
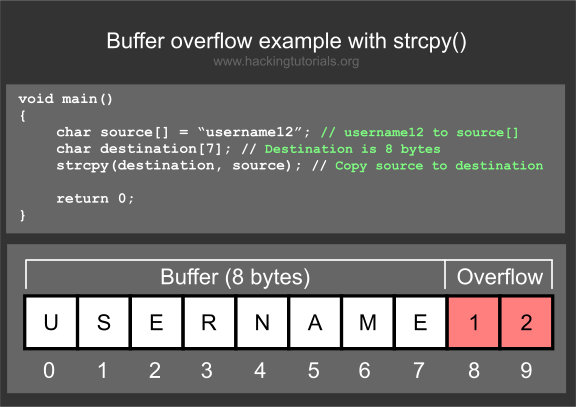
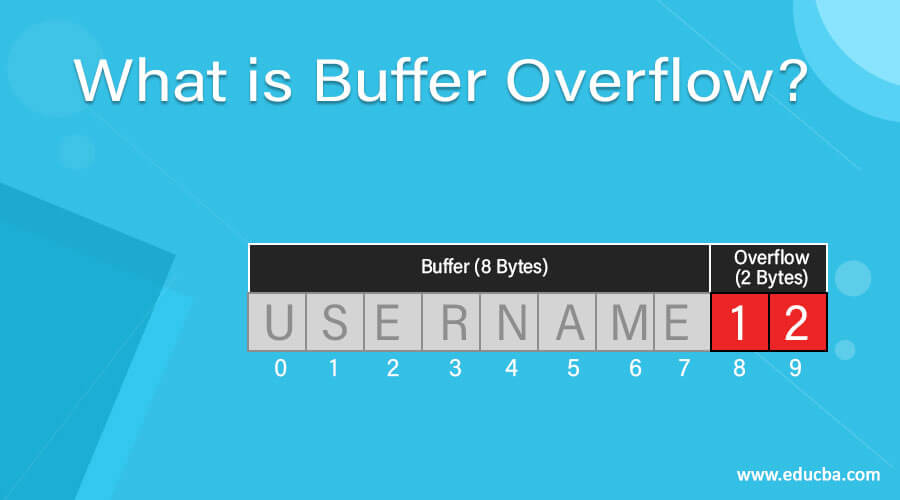
How to detect buffer overrun. Buffer overflow attacks generally need to know where the executable code is located. You can use codeql to detect potential buffer overflows by checking for allocations equal to strlen in c and c++. A buffer overrun is essentially caused by treating unchecked, external input as trustworthy data.
The message that showed, it is a buffer overrun problem was. A buffer overrun is one of the most common sources of security risk. Using the registry editor to change system settings the registry editor is a tool in windows.
This causes a bug check when a program tries to access memory beyond its special pool memory. You are seeing an improvement to the /gs mechanism, first added to vs2012. At a certain point before the.
In the configure behavior monitoring dialog box: According to the msdn library, when you compile c or c++ source code by using the visual c++ 2013 c/c++ compiler, visual c++ 2013 should detect some buffer overrun scenarios (of. In the late 1980s, a buffer overflow in unix’s fingerd program allowed robert t.
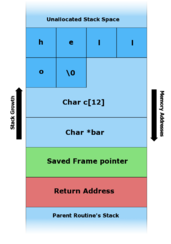
Canaries are inserted at compile time to help detect buffer overflows by inserting a word of data between a buffer and the control data on the stack. Beside enable behavior monitoring, click configure. To alert the administrator and block buffer overflows, select the detect buffer overflows.
Address space layout randomization (aslr) moves at random around data region locations to.